The artificial intelligence gold rush has brought incredible tools to our fingertips, streamlining everything from customer service to content creation. Unfortunately, this technological boom has also paved a golden highway for cybercriminals. As enthusiasm for AI grows, so does the sophistication of digital threats. Recent data paints a concerning picture: …
Hidden Business Costs of Employee Social Media Oversharing
Social media has fundamentally shifted how businesses and employees interact with the world. While these platforms are incredible tools for brand building and networking, they also introduce a vector for risk that many organizations overlook until it is too late. When employees share content online, they often blur the lines …
Essential Steps to Protect Your Company’s Connected Technology
Walk into any modern office and you’ll find dozens of connected devices quietly humming away: smart thermostats adjusting the temperature, security cameras monitoring entry points, intelligent lighting systems responding to occupancy, and networked printers handling sensitive documents. These Internet of Things (IoT) devices have become essential business tools, streamlining operations …
Understanding Card Skimming and Its Impact on Your Businesses
When you think of data security, you likely picture firewalls, antivirus software, and complex passwords. However, one of the most persistent threats to your company’s financial health operates in the physical world just as often as it does in the digital one. Card skimming is a method where thieves capture …
Holiday Cybersecurity: Protecting Your Business from Seasonal Scams and Fraud
The end of the year brings a unique energy to the office. While your team is focused on closing Q4 strong, hitting end-of-year targets, and planning holiday parties, cybercriminals are gearing up for what they consider their most profitable season. It is a harsh reality that the festivity of the …
A Guide to AI Safety and Security in the Workplace
Artificial intelligence has moved from the realm of science fiction to everyday business reality faster than most of us could have imagined. What started as experimental technology is now woven into the fabric of how companies operate, from drafting emails to analyzing market trends to automating customer service. This rapid …
How Cybercriminals Use Your Digital Footprint Against Your Business
Your business has an invisible presence online that extends far beyond your website and social media accounts. Every digital interaction, from employee LinkedIn profiles to customer reviews, contributes to your company’s digital footprint. While this online presence is essential for modern business operations, it also creates opportunities for cybercriminals to …
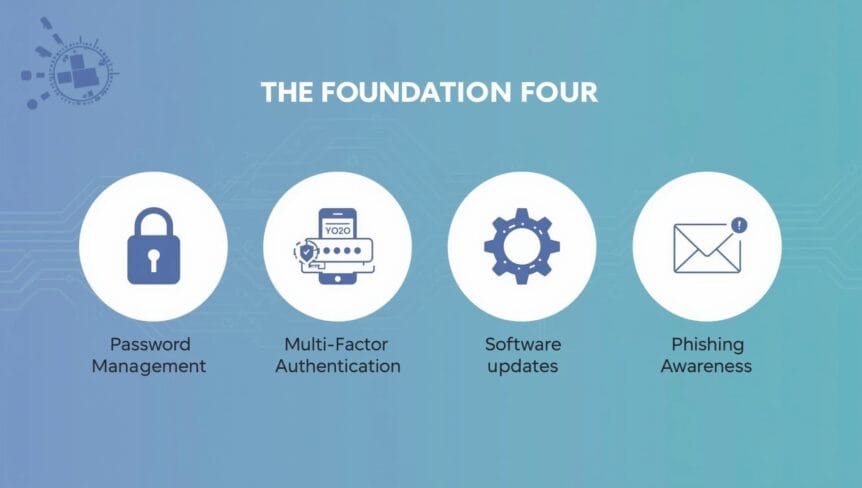
Essential Digital Security Fundamentals Every Business Professional Should Master
Cybercriminals have dramatically shifted their targeting strategies in 2025, with small and medium businesses bearing a substantial share of attacks, roughly 43–50% depending on the study you look at. The myth that hackers only pursue large corporations has been thoroughly debunked as criminals increasingly recognize that smaller organizations often lack …
How Florida Businesses Can Protect Against Charity Scams
Florida companies face unique challenges when it comes to charitable giving. While corporate philanthropy strengthens community ties and fulfills social responsibility goals, it also makes organizations prime targets for sophisticated charity scams. With hurricane season, holiday giving, and year-round fundraising appeals, the business community must balance generosity with vigilance. The …
How to Protect Your Business from Deepfake Fraud
Artificial intelligence has transformed from science fiction into a powerful tool for both legitimate business applications and sophisticated criminal schemes. Among the most concerning developments is the rise of deepfake fraud, where AI technology creates convincing fake videos, images, and audio that can be nearly indistinguishable from authentic media. Understanding …