Understanding the Dark Web The dark web represents a hidden layer of the internet, accessible only through specialized browsers and encryption tools like Tor (The Onion Router) or I2P (Invisible Internet Project). Understanding the dark web isn’t just about technical curiosity – it’s about recognizing a significant source of cyber …
Cybersecurity Predictions for 2025: Challenges and Opportunities
The year 2024 was a whirlwind year for cybersecurity. From the fallout of high-profile ransomware attacks to the increasing commoditization of AI tools, the challenges kept mounting. Critical infrastructure vulnerabilities became starkly apparent, and identity theft reached unprecedented levels. Yet, amidst the chaos, we saw strides in defensive technologies, international …
Chrome 127’s Enhanced Security Features and Challenges
Discover how Chrome 127 aims to protect over 3.5 billion users from cyber threats with its new infostealer malware block while hackers find new ways to exploit vulnerabilities.
New Malware Disguised as VPN Threatens Businesses
Learn about the latest malware campaign posing as Palo Alto GlobalProtect VPN and find out how to prevent cyber threats with our expert tips. Keep your data secure.
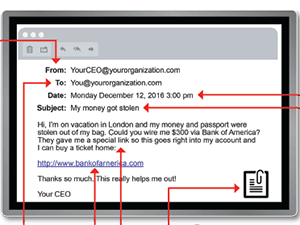
How To Recognize The Phishing Clues
In recognition of Cybersecurity Awareness Month, we wanted to share this guide for spotting a phishing email. The best way to avoid falling for phishing emails and clicking where you shouldn’t is to recognize the red flags. We recommend printing this guide and keeping it handy so you can spot …
Quick Take On Keeping Your Mobile Devices Secure
As remote work and connecting while traveling has become the norm, mobile device security responsibilities have also increased. We take our smartphones, tablets and laptops to airports, cafes and other public places, so the threat of a cyber attack targeting our devices is constant. There are some best practices to …
Half of Employees Fear Reporting Cybersecurity Mistakes
In the fast-paced world of business, mistakes are inevitable. Yet, when cybersecurity errors occur, many employees hesitate to report them. An estimated 50% of employees are afraid to report their cybersecurity errors because they dread the repercussions according to a report by ThinkCyber. This reluctance can seriously affect organizations, potentially …
Protect Your Business from Advanced Info Stealer Malware
Discover how to safeguard your organization’s sensitive data from sophisticated malware campaigns. Learn effective strategies for email security, staff education, and comprehensive security tools.
Protect Your Business from EDRKillShifter Malware
EDRKillShifter malware neutralizes EDR systems, leaving businesses vulnerable. Learn essential strategies to protect your organization from this rising cyber threat.
Combatting Social Engineering and FakeBat Loader Malware
Discover how social engineering and FakeBat Loader malware work, and learn best practices for protecting your business from these advanced cyber threats.