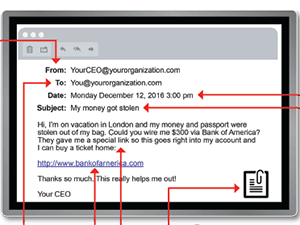
In recognition of Cybersecurity Awareness Month, we wanted to share this guide for spotting a phishing email. The best way to avoid falling for phishing emails and clicking where you shouldn’t is to recognize the red flags. We recommend printing this guide and keeping it handy so you can spot …
GPT-3 Makes Phishing Scams Like These Worse
Phishing attacks have reached a new high, with cybercriminals favoring various phishing techniques to trap their victims in nasty phishing scams. Hackers use different phishing techniques as a precursor to many devastating cyberattacks like ransomware, business email compromise (BEC), malware and account takeover. As perpetrators use deceiving social engineering lures, …
New Wave of Supply Chain Cyber Attacks Expected
Throughout April, Shanghai and other major cities in China have been on lockdown due to recent COVID-19 outbreaks. Along with the ongoing war in Ukraine, these lockdowns have drastically impacted supply chains for industries around the world. We expect to see another wave of supply chain-related phishing and social engineering …
10 Facts About the Benefits of Security Awareness Training
Are you looking for an affordable, effective way to protect your company from cyberattacks and prevent a data breach? In today’s volatile cyberattack landscape, every business in every industry is at risk of a cyberattack. That means that every business needs to make sure that it’s taking a strong defensive …
Ho-Ho-Hoax!
The Top Five Holiday Cyber Scams The holiday season is when retailers make most of their money. Cybercriminals, too. We’re making a list (and checking it twice) of the most widely used holiday cyber scams. Have a look: Bogus e-cards. Hallmark recently got out of the electronic greeting card business, …
How to Boost Your Business’ Success in 3 Easy Steps
Running a Business is Never Easy There are so many moving parts to juggle and decisions to prioritize, it can be easy to skip over key steps on the path to success. While good business savvy is obviously a key requirement for this success to happen, there are certain things …