Gift cards make for easy, versatile gifts, especially during the busy holiday season. But they’re also prime targets for scammers who use “gift card draining” to steal funds before the recipient can even use the card. Let’s break down how these scams work and how you can stay safe. What …
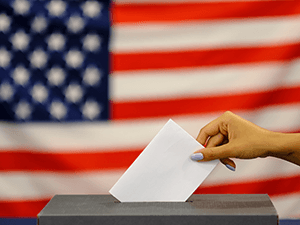
Election-Themed Scams Are on the Rise
Researchers at Malwarebytes warn of a surge in election-themed scams ahead of November’s presidential election in the US. These attacks can be expected to increase as the election grows closer. “The lure that we have seen the most involves asking people to donate to a campaign,” Malwarebytes says. “Whether that …
ATTENTION: Cyber Warning For Our Clients
We wanted to alert you to a cybersecurity threat our engineers have successfully mitigated for several of our clients recently. We’ve seen a rise in a specific type of cyber risk: malicious email links and attachments that appear to come from coworkers and other trusted sources like regular vendors or …
Security-Savvy Employees Are Critical For Cyber Resilience
In chess, two rows of pieces are placed on either side of the board. These rows consist of eight pawns as the first line of defense against the enemy. The rest of the pieces behind them can move about effectively, depending on how you direct your pawns. But what if …
FBI and FCC Cautions On Juice Jacking
The Federal Bureau of Investigation (FBI) and the Federal Communications Commission (FCC) are warning the public about the dangers of “juice jacking.” Juice jacking occurs when someone innocently plugs their phone or mobile device into a compromised USB port that is infected with malicious software. Such malware can allow criminals …
What Are The Dangers of Business Email Compromise?
What’s the most expensive cyberattack that businesses face today? If you said business email compromise (BEC) you’re right. The FBI IC3 2021 Internet Crime Report showed that BEC packed a powerful punch against U.S. businesses that year. BEC complainants to IC3 suffered $2,395,953,296 in losses in 2021, 28% higher than …
New Wave of Supply Chain Cyber Attacks Expected
Throughout April, Shanghai and other major cities in China have been on lockdown due to recent COVID-19 outbreaks. Along with the ongoing war in Ukraine, these lockdowns have drastically impacted supply chains for industries around the world. We expect to see another wave of supply chain-related phishing and social engineering …
New Wave of Cyber Attacks Likely
According to the U.S. government, Russia is poised to unleash a massive wave of malware in retaliation for sanctions imposed after an invasion of Ukraine. The Cybersecurity & Infrastructure Security Agency warns that, unlike targeted cyber operations, malware attacks spread ubiquitously. That means a small business is far more likely …
Windows 7 Support Officially Ends Today
Windows 7 End of Life has arrived. Microsoft is ending support for this aging operating system on January 14, 2020. This means a decade after introducing Windows 7, Microsoft will no longer provide security updates or patches unless you purchase Extended Security Updates from Microsoft. Tech support from Microsoft for …
Windows 7 And Our Clients
A decade after introducing Windows 7, Microsoft is ending support for this aging operating system on January 14, 2020. As our client, we are conducting a thorough audit of your resources to determine how the end of Windows 7 will impact your network. Once an operating system enters end-of-life status, Microsoft …
- Page 1 of 2
- 1
- 2