The Rise of Executive-Targeted Award Scams A sophisticated phishing campaign uncovered by Trustwave SpiderLabs researchers is making the rounds, and it is specifically designed to fool senior executives. The scheme impersonates the prestigious luxury brand Cartier, presenting targets with a fabricated “Cartier Recognition Program” that promises exclusive professional recognition. This …
New LinkedIn Phishing Scam Uses Fake Policy Violation Comments to Steal Business Credentials
A sophisticated phishing campaign is currently targeting LinkedIn users through an elaborate scheme that exploits the platform’s comment system. Unlike traditional email-based phishing, these cybercriminals are posting fake policy violation warnings directly on user posts, creating an alarming new threat vector for business professionals. Security researchers have identified multiple instances …
How Cybercriminals Are Exploiting Email System Weaknesses to Send Fake Internal Messages
When your accounting manager receives an email from your CEO requesting an urgent wire transfer, they’re likely to act quickly. When HR sends a message about updating direct deposit information, employees typically click without hesitation. This trust in internal communications is exactly what cybercriminals are exploiting through increasingly sophisticated email …
Holiday Cybersecurity: Protecting Your Business from Seasonal Scams and Fraud
The end of the year brings a unique energy to the office. While your team is focused on closing Q4 strong, hitting end-of-year targets, and planning holiday parties, cybercriminals are gearing up for what they consider their most profitable season. It is a harsh reality that the festivity of the …
How Florida Businesses Can Protect Against Charity Scams
Florida companies face unique challenges when it comes to charitable giving. While corporate philanthropy strengthens community ties and fulfills social responsibility goals, it also makes organizations prime targets for sophisticated charity scams. With hurricane season, holiday giving, and year-round fundraising appeals, the business community must balance generosity with vigilance. The …
How to Protect Your Business from Deepfake Fraud
Artificial intelligence has transformed from science fiction into a powerful tool for both legitimate business applications and sophisticated criminal schemes. Among the most concerning developments is the rise of deepfake fraud, where AI technology creates convincing fake videos, images, and audio that can be nearly indistinguishable from authentic media. Understanding …
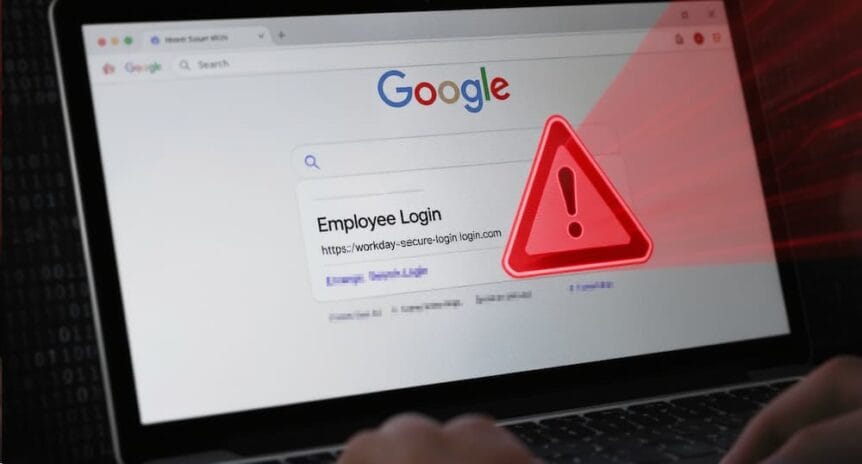
How Cybercriminals Are Stealing Paychecks Through Fake Google Ads
It’s payday Friday, and you realize you need to update your tax withholding information. You quickly Google your company’s benefits portal, click the first link that appears, log in, and go about your day. A week later, your paycheck never arrives. What happened? You’ve just become a victim of a …
How Cybercriminals Use Images in Phishing Emails to Bypass Security
Fraudsters have elevated their phishing tactics to new levels of sophistication, particularly when it comes to using images to bypass security measures and trick your employees. These visual deception strategies have become increasingly effective at compromising business credentials, stealing sensitive data, and infiltrating company networks. Understanding how these attacks work …
Beware QR Code Package Scams
When a mysterious package arrives at your business address, curiosity might be your first reaction. However, federal authorities are warning business owners about a sophisticated cybersecurity threat that combines old-school mail fraud with modern digital attacks: QR code package scams. These unsolicited packages typically arrive with minimal identifying information and …
New Instagram Phishing Scam Uses Email Tricks to Bypass Security
A sophisticated phishing campaign targeting Instagram users has emerged, using clever email tactics to bypass traditional security measures. This new threat uses “mailto” links instead of conventional phishing URLs, making it particularly dangerous for businesses with social media presence. Understanding how this attack works and implementing proper protection strategies is …
- Page 1 of 2
- 1
- 2