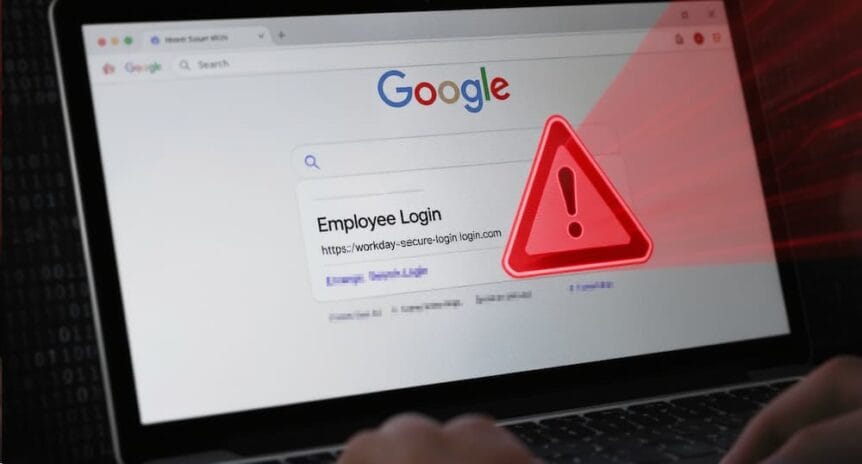
It’s payday Friday, and you realize you need to update your tax withholding information. You quickly Google your company’s benefits portal, click the first link that appears, log in, and go about your day. A week later, your paycheck never arrives. What happened? You’ve just become a victim of a sophisticated malvertising attack that’s increasingly targeting employees across the country.
Malvertising, short for malicious advertising, occurs when cybercriminals inject harmful code or deceptive content into legitimate online advertising networks. Unlike traditional scams that rely on suspicious emails or obvious fake websites, malvertising exploits our trust in established platforms like Google Ads to deliver convincing fraudulent content.
The FBI reported a 300% increase in paycheck redirect schemes in the past year alone, with businesses of all sizes falling victim. These attacks specifically target employees searching for their company’s HR, payroll, or benefits portals, with the average loss per victim exceeding $3,200, according to recent cybersecurity reports.
Small businesses are particularly vulnerable. Documented cases show payroll diversion can quickly result in five-figure losses per incident, with additional costs for forensic investigation and remediation. Even a single compromised login can have outsized financial impact.
How the Paycheck Theft Scam Actually Works
The attack is remarkably straightforward yet devastatingly effective:
First, attackers purchase Google Ads targeting specific keywords related to popular employee portal platforms like Workday, ADP, Paychex, or UKG. They bid on terms like “company name + employee login” or “Workday portal login,” ensuring their malicious ads appear at the top of search results.
When an employee searches for their company’s portal and clicks the sponsored ad (which looks nearly identical to legitimate search results), they’re directed to a convincing replica of the actual login page. These fake pages are meticulously designed to match the real portal’s appearance, often hosted on domains that seem plausible at a glance, like “workday-secure-login.com” or “adp-employee-access.net.”
Once the unsuspecting employee enters their username and password, the attackers capture these credentials in real-time. Some sophisticated operations even pass these credentials to the actual portal simultaneously, creating a seamless experience where the employee successfully logs in and notices nothing unusual.
With valid credentials in hand, attackers later access the legitimate portal, navigate to the direct deposit section, and change the banking information to accounts they control. When the next payroll runs, the funds are diverted to the fraudsters instead of the employee’s account.
Why This Attack Method Is So Effective
The genius of this attack lies in its exploitation of our established online behaviors and trust in familiar systems. When we see Google search results, particularly sponsored ads at the top of the page, we inherently trust that Google has vetted these advertisers, which simply isn’t the case.
Modern phishing sites have evolved far beyond the obvious scams of years past. Today’s fraudulent portals feature pixel-perfect recreations of legitimate websites, complete with functioning password strength meters, “forgot password” links, and even privacy policies. Some attacks employ “session hijacking” techniques that can intercept and defeat two-factor authentication by capturing and reusing authentication tokens in real-time.
The financial motivation is substantial; a single successful attack on a medium-sized business can yield tens of thousands of dollars in a single payroll cycle. While targeted lures like these often outperform generic phishing, published industry reports typically find average click/compromise rates in the low single digits. Even small percentages translate into major losses when attackers aim at payroll and benefits systems.
Recognizing Red Flags: How to Spot Fake Employee Portal Ads and Login Pages
Protecting yourself starts with knowing what to look for before you click. Remember that cybercriminals are counting on your hurry and distraction to bypass your natural skepticism.
The most important rule: Never trust search results (even Google’s) to access sensitive company portals. Always verify before you click, and when in doubt, go directly to your company’s official website or intranet first.
Identifying Suspicious Google Ads
Legitimate companies rarely need to advertise their own employee login portals, so sponsored results for specific employee portal searches should immediately raise suspicion. Before clicking any ad:
- Check the actual destination URL shown in the ad (usually in small text below the headline) for subtle misspellings or unusual domains.
- Hover your mouse over any link to preview where it will actually take you, looking for discrepancies between the displayed text and the actual URL.
- Note the domain structure: legitimate company portals usually use their primary domain (like company.com/portal) or a specific subdomain (portal.company.com), not standalone domains.
- Be wary of domains that add terms like “secure,” “login,” or “access” to mimic legitimate services (e.g., “workday-secure.com” instead of “workday.com”).
One telltale sign of fraudulent ads is the use of urgent language or special offers related to employee benefits or payroll, which legitimate companies rarely promote through Google Ads.
Warning Signs of Fake Login Pages
Even if you’ve clicked a suspicious link, you can still protect yourself by recognizing these warning signs before entering credentials:
Look for subtle visual inconsistencies like slightly off-color logos, unusual font choices, or alignment issues that differ from the legitimate site. Fraudulent sites often get these details wrong.
Check the security indicators in your browser: legitimate portals will always use HTTPS (look for the padlock icon in your address bar). If you see “Not Secure” or missing security indicators, close the page immediately.
Be suspicious of login pages that ask for more information than usual, such as your complete social security number, bank account details, or personal identifying information beyond your standard username and password.
Pay attention to how multi-factor authentication is handled. If a site that normally requires a second verification step suddenly doesn’t, or if the MFA process looks different than usual, this could indicate a fake portal.
Best Practices for Safe Access to Employee Portals and Online Accounts
Prevention is always better than recovery when it comes to cybersecurity. Establishing secure access habits isn’t just good personal practice; it’s essential for protecting your company’s entire network and financial systems.
Secure Login Procedures for Employees
Create a secure bookmark for your employee portal in your browser and use it exclusively, rather than searching each time you need access. Take a few minutes to do this on each device you regularly use.
If you must search, go to your company’s main website first, then navigate to the portal login from there, rather than searching directly for the portal.
When accessing portals from home or public networks, consider using your company’s VPN if available to add an extra layer of security to your connection.
Establish a verification routine: before entering credentials, always check the URL and security indicators, no matter how legitimate the page appears. This simple habit can prevent most credential theft attempts.
Don’t hesitate to contact your IT or HR department if anything seems unusual about the portal. Most security teams would rather answer a false alarm than deal with a successful attack.
Essential Security Measures for Account Protection
Use unique, complex passwords for all work-related accounts, especially those connected to payroll or benefits. Consider using a password manager to help maintain different passwords across multiple systems.
Enable multi-factor authentication on all accounts that offer it, preferably using an authenticator app rather than SMS text messages, which can be intercepted.
Regularly review your account settings, particularly direct deposit information, and set calendar reminders to check these details before major payroll periods.
Log out completely from portals when finished, especially on shared or public computers, and clear your browser cache periodically to remove stored login information.
What to Do If You Suspect You’ve Been Targeted or Compromised
Even with the best precautions, attacks can sometimes succeed. Your response in the first 24-48 hours can make a significant difference in limiting damage and recovering funds.
Immediate Response Steps for Individuals
If you suspect you’ve entered credentials on a fraudulent site, immediately change your password on the legitimate portal and any other accounts where you’ve used the same password.
Contact your HR and payroll departments immediately, even outside business hours. Explain what happened and ask them to verify and lock your direct deposit information to prevent unauthorized changes.
Call your bank to alert them to potential fraudulent activity and consider placing a temporary freeze on your accounts if payroll is imminent.
Document everything: take screenshots of the suspicious site if still available, note the URL, and record the time and date of the incident to help with any subsequent investigation.
Organizational Response and Recovery
For businesses, having a well-defined incident response plan is critical. When an employee reports a potential compromise:
Immediately lock the affected employee accounts and force password resets while your IT team investigates the scope of the breach.
Contact your payroll provider and banking partners to place holds on upcoming payroll processing or implement additional verification steps for any direct deposit changes.
Consider sending an organization-wide alert about the specific attack, with screenshots if available, to warn other employees who may have been targeted but haven’t yet reported it.
Work with your financial institutions to attempt recovery of any diverted funds, which is sometimes possible if reported quickly enough.
Protecting Your Business: Advanced Strategies for Organizations
For business owners and IT leaders, defending against these sophisticated attacks requires a layered approach combining technical controls and human awareness.
Technical Security Measures
Implement advanced endpoint protection on all company devices that can detect and block malicious websites, even those delivered through legitimate advertising networks.
Consider deploying DNS filtering or secure web gateways that can block connections to known malicious domains before employees even reach the fake portal.
Enforce strong authentication policies, including multi-factor authentication for all employee portal access, preferably with phishing-resistant methods like security keys when possible.
Conduct regular security assessments of your HR and payroll systems, including simulated phishing tests targeting your specific employee portals to identify vulnerabilities before attackers exploit them.
Employee Education and Awareness Programs
Develop targeted training that specifically addresses payroll redirect scams and malvertising, not just generic phishing awareness. Show real examples of what these attacks look like.
Conduct regular phishing simulations that include scenarios mimicking these specific attacks, followed by immediate training for employees who fall for the simulated phish.
Create a simple, blame-free reporting process for employees to alert security teams about suspicious sites or potential credential compromises without fear of punishment.
Establish regular communication channels to keep employees updated on current threats, perhaps through a monthly security bulletin or inclusion in regular company communications.
Remember that protecting your business from paycheck theft through malvertising isn’t just about technology; it’s about creating a security-conscious culture where employees feel empowered to question suspicious activities and follow secure practices consistently. By combining the right tools with effective human awareness, you can significantly reduce your organization’s risk of falling victim to these increasingly sophisticated attacks.
At I.T. Solutions of South Florida, we help businesses implement comprehensive security strategies to defend against threats like malvertising and paycheck theft. Contact us today to learn how we can help protect your organization’s financial assets and employee data from these evolving cyber threats.