Artificial intelligence has moved from the realm of science fiction to everyday business reality faster than most of us could have imagined. What started as experimental technology is now woven into the fabric of how companies operate, from drafting emails to analyzing market trends to automating customer service. This rapid …
How Cybercriminals Use Your Digital Footprint Against Your Business
Your business has an invisible presence online that extends far beyond your website and social media accounts. Every digital interaction, from employee LinkedIn profiles to customer reviews, contributes to your company’s digital footprint. While this online presence is essential for modern business operations, it also creates opportunities for cybercriminals to …
Essential Digital Security Fundamentals Every Business Professional Should Master
Cybercriminals have dramatically shifted their targeting strategies in 2025, with small and medium businesses bearing a substantial share of attacks, roughly 43–50% depending on the study you look at. The myth that hackers only pursue large corporations has been thoroughly debunked as criminals increasingly recognize that smaller organizations often lack …
How Florida Businesses Can Protect Against Charity Scams
Florida companies face unique challenges when it comes to charitable giving. While corporate philanthropy strengthens community ties and fulfills social responsibility goals, it also makes organizations prime targets for sophisticated charity scams. With hurricane season, holiday giving, and year-round fundraising appeals, the business community must balance generosity with vigilance. The …
How to Protect Your Business from Deepfake Fraud
Artificial intelligence has transformed from science fiction into a powerful tool for both legitimate business applications and sophisticated criminal schemes. Among the most concerning developments is the rise of deepfake fraud, where AI technology creates convincing fake videos, images, and audio that can be nearly indistinguishable from authentic media. Understanding …
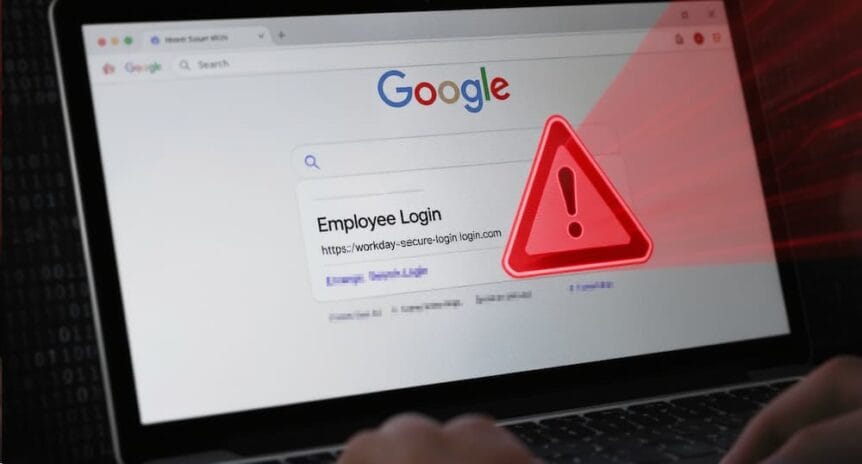
How Cybercriminals Are Stealing Paychecks Through Fake Google Ads
It’s payday Friday, and you realize you need to update your tax withholding information. You quickly Google your company’s benefits portal, click the first link that appears, log in, and go about your day. A week later, your paycheck never arrives. What happened? You’ve just become a victim of a …
The Hidden Costs of Running Microsoft Office Without Professional IT Support
Most businesses today rely heavily on Microsoft Office for their daily operations, yet many underestimate the true cost of running these essential tools without proper professional support. While the upfront licensing fees are obvious, the hidden expenses of inadequately managed Office environments can silently drain your resources and threaten your …
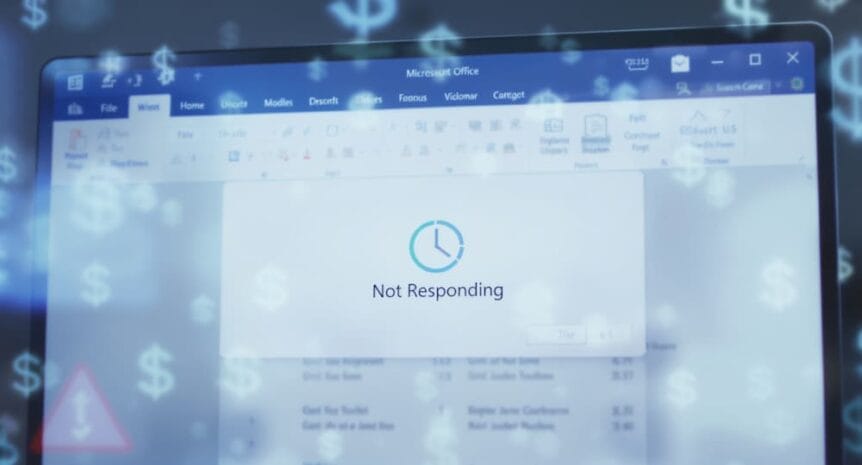
The Ransomware Paradox: Why Fewer Attacks Are Costing Businesses More Than Ever
The world of cybersecurity is facing a perplexing contradiction: businesses are experiencing fewer ransomware attacks than before, yet the financial damage from these incidents is skyrocketing. This unexpected development has security experts and business leaders alike questioning traditional assumptions about cyber defense and risk management. The Current Ransomware Landscape: A …
How Cybercriminals Use Images in Phishing Emails to Bypass Security
Fraudsters have elevated their phishing tactics to new levels of sophistication, particularly when it comes to using images to bypass security measures and trick your employees. These visual deception strategies have become increasingly effective at compromising business credentials, stealing sensitive data, and infiltrating company networks. Understanding how these attacks work …
Beware QR Code Package Scams
When a mysterious package arrives at your business address, curiosity might be your first reaction. However, federal authorities are warning business owners about a sophisticated cybersecurity threat that combines old-school mail fraud with modern digital attacks: QR code package scams. These unsolicited packages typically arrive with minimal identifying information and …