Florida companies face unique challenges when it comes to charitable giving. While corporate philanthropy strengthens community ties and fulfills social responsibility goals, it also makes organizations prime targets for sophisticated charity scams. With hurricane season, holiday giving, and year-round fundraising appeals, the business community must balance generosity with vigilance. The …
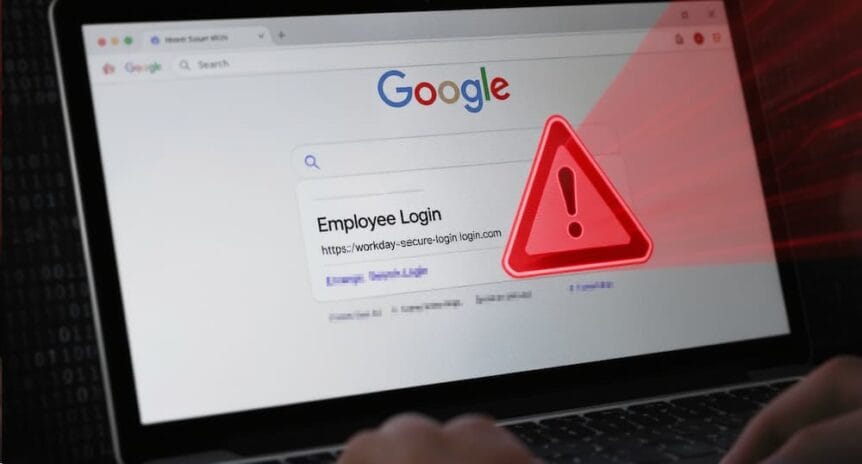
How Cybercriminals Are Stealing Paychecks Through Fake Google Ads
It’s payday Friday, and you realize you need to update your tax withholding information. You quickly Google your company’s benefits portal, click the first link that appears, log in, and go about your day. A week later, your paycheck never arrives. What happened? You’ve just become a victim of a …
The Ransomware Paradox: Why Fewer Attacks Are Costing Businesses More Than Ever
The world of cybersecurity is facing a perplexing contradiction: businesses are experiencing fewer ransomware attacks than before, yet the financial damage from these incidents is skyrocketing. This unexpected development has security experts and business leaders alike questioning traditional assumptions about cyber defense and risk management. The Current Ransomware Landscape: A …
How Cybercriminals Use Images in Phishing Emails to Bypass Security
Fraudsters have elevated their phishing tactics to new levels of sophistication, particularly when it comes to using images to bypass security measures and trick your employees. These visual deception strategies have become increasingly effective at compromising business credentials, stealing sensitive data, and infiltrating company networks. Understanding how these attacks work …
Beware QR Code Package Scams
When a mysterious package arrives at your business address, curiosity might be your first reaction. However, federal authorities are warning business owners about a sophisticated cybersecurity threat that combines old-school mail fraud with modern digital attacks: QR code package scams. These unsolicited packages typically arrive with minimal identifying information and …
How to Protect Your Business from Ransomware and Malware Attacks in 2025
Ransomware and malware attacks continue to pose significant threats to businesses of all sizes. As cybercriminals refine their tactics, organizations must stay vigilant and implement robust protection strategies. The financial impact is staggering; recent data shows ransomware claim severity jumped by 68% this year, with average losses reaching $353,000 per …
Cybersecurity Challenges in Mergers and Acquisitions
Mergers and acquisitions offer tremendous growth opportunities for businesses of all sizes, but they also create significant cybersecurity vulnerabilities that can undermine deal value and expose organizations to unexpected risks. As companies combine forces, their digital ecosystems merge as well, often revealing security gaps that cybercriminals are eager to exploit. …
Protecting Your Business Data When Using AI Tools
Artificial intelligence has transformed how businesses operate, enabling unprecedented levels of productivity and innovation. As these powerful tools become integral to daily workflows, they also create new vulnerabilities that could expose your valuable business information. Understanding these risks and implementing proper safeguards is essential for any organization utilizing AI technologies. …
Why Your Business Needs Passkeys: The Security Solution That’s Replacing Passwords in 2025
The cybersecurity landscape has fundamentally changed, and password-based security is no longer adequate to protect your business. Passkeys represent the most significant advancement in authentication technology of the past decade, offering a solution that’s both more secure and more user-friendly than traditional passwords. The Password Crisis Threatening Your Business Password-related …
Protecting Your Company from Sophisticated WhatsApp Scams
WhatsApp has become an essential business communication tool, but this widespread adoption has made it a prime target for cybercriminals. As sophisticated scam techniques evolve, businesses face increasing risk of financial loss, data theft, and reputational damage through this popular platform. Understanding these threats and implementing robust protection strategies is …