The end of the year brings a unique energy to the office. While your team is focused on closing Q4 strong, hitting end-of-year targets, and planning holiday parties, cybercriminals are gearing up for what they consider their most profitable season. It is a harsh reality that the festivity of the …
The Ransomware Paradox: Why Fewer Attacks Are Costing Businesses More Than Ever
The world of cybersecurity is facing a perplexing contradiction: businesses are experiencing fewer ransomware attacks than before, yet the financial damage from these incidents is skyrocketing. This unexpected development has security experts and business leaders alike questioning traditional assumptions about cyber defense and risk management. The Current Ransomware Landscape: A …
How Cybercriminals Use Images in Phishing Emails to Bypass Security
Fraudsters have elevated their phishing tactics to new levels of sophistication, particularly when it comes to using images to bypass security measures and trick your employees. These visual deception strategies have become increasingly effective at compromising business credentials, stealing sensitive data, and infiltrating company networks. Understanding how these attacks work …
How to Protect Your Business from Ransomware and Malware Attacks in 2025
Ransomware and malware attacks continue to pose significant threats to businesses of all sizes. As cybercriminals refine their tactics, organizations must stay vigilant and implement robust protection strategies. The financial impact is staggering; recent data shows ransomware claim severity jumped by 68% this year, with average losses reaching $353,000 per …
How Cybercriminals Are Using AI to Launch More Sophisticated Attacks Against Your Business
Artificial intelligence has fundamentally transformed the cybersecurity landscape, creating both remarkable defensive capabilities and unprecedented threats. While security professionals leverage AI to protect digital assets, cybercriminals have eagerly embraced these same technologies to develop increasingly sophisticated attack strategies that bypass traditional security measures. The Growing Threat: AI-Powered Cybercrime in 2025 …
Building a Strong Cybersecurity Culture in Your Organization
According to a recent CyberEdge Group survey, organizations consistently cite low security awareness among employees as the single biggest barrier to defending against cyberattacks. This finding reinforces what cybersecurity professionals have long understood: human challenges consistently trump technology issues when it comes to protecting digital assets. Despite billions spent annually …
A Comprehensive Guide to the Dark Web
Understanding the Dark Web The dark web represents a hidden layer of the internet, accessible only through specialized browsers and encryption tools like Tor (The Onion Router) or I2P (Invisible Internet Project). Understanding the dark web isn’t just about technical curiosity – it’s about recognizing a significant source of cyber …
Cybersecurity Predictions for 2025: Challenges and Opportunities
The year 2024 was a whirlwind year for cybersecurity. From the fallout of high-profile ransomware attacks to the increasing commoditization of AI tools, the challenges kept mounting. Critical infrastructure vulnerabilities became starkly apparent, and identity theft reached unprecedented levels. Yet, amidst the chaos, we saw strides in defensive technologies, international …
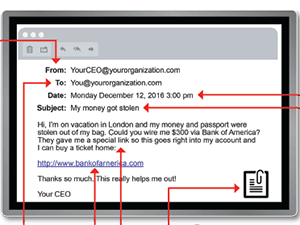
How To Recognize The Phishing Clues
In recognition of Cybersecurity Awareness Month, we wanted to share this guide for spotting a phishing email. The best way to avoid falling for phishing emails and clicking where you shouldn’t is to recognize the red flags. We recommend printing this guide and keeping it handy so you can spot …
Quick Take On Keeping Your Mobile Devices Secure
As remote work and connecting while traveling has become the norm, mobile device security responsibilities have also increased. We take our smartphones, tablets and laptops to airports, cafes and other public places, so the threat of a cyber attack targeting our devices is constant. There are some best practices to …